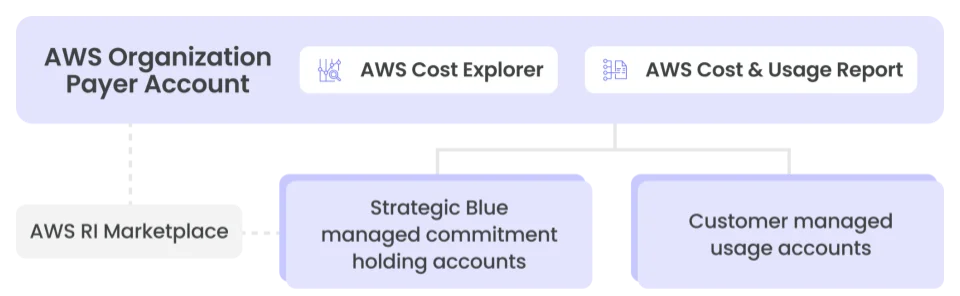
The access needed to deliver our rate optimization services is described in relation to standard AWS Accounts, Organization and reporting structures:
The templates below provide the technical detail of the clearly defined roles, each for a dedicated Strategic Blue authentication account, which acts as a bastion service.
Read data about the payer account
We can list organization accounts and their tags, describe Cost and Usage Report definitions and read the S3 bucket that holds those reports (template).
We only collect data regarding billing and instances such as the quantity, class and region as this will enable us to make recommendations. We use this to provide our recommendations, apply discounts and produce your insights and usage dashboard for reporting.
Review data with “AWS Billing and Cost Management”
We verify our optimization actions have been correctly applied by AWS, view usage, billing and savings plan information (template).
Commitment-holding account access control
We buy, change and sell reserved instance and savings plan commitments in dedicated holding accounts. These accounts are created specifically for us. They generate no usage and are used to isolate our activities, simplify auditing and create clear commitment ownership. We have admin access to these accounts.
Reserved Instance Marketplace
We grant our commitment holding accounts the ability to sell unused Reserved Instance commitments when required on the AWS Reserved Instance Marketplace (template). This is optional for customers where we are not also the AWS reseller.